E-signature
The most common method of securing electronic payments is using cryptographic-based technologies such as encryption and electronic signatures. An electronic signature (e-signature) is a string of data that is attached to an electronic message in order to guarantee its authenticity, identify the signatory and link the content to that signatory (thereby protecting the recipient against repudiation by the sender). The e-signature provides an effective means of guaranteeing the authenticity and integrity of any document during its life and its importance has been stressed in UNECE Recommendation No. 35- Establishing a Legal Framework for an International Trade Single Window.
Electronic signatures have an impact throughout the entire invoicing process:
- Creation: to ensure authenticity and integrity of the document, electronic signatures have to be applied when creating an invoice,
- Exchange: for the receiver to validate an electronic signature, signature validation information has to be sent with the invoice document,
- Acceptance: to validate the authenticity and integrity of the received invoice, the receiver can (depending on national legislation) validate the electronic signature using the information available,
- Storage: invoices have to be stored for a period of time as required by local tax authorities. Authenticity of origin and integrity of data must be ensured for the stored invoice.
Implementation guidance
The implementation infrastructure, commonly referred to as the Public Key Infrastructure (PKI), requires each user to have a public-private key pair where the public key is available to the world, while the private key is only known by the user. The following is an example of a digital signature scenario.
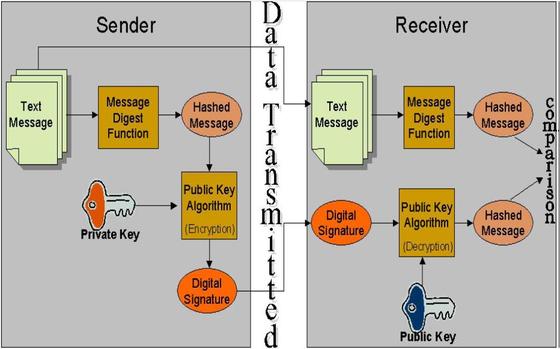
The sender wants to send the receiver a text message with a digital signature. First, the sender creates the text message to be signed and generates a hashed message, using a specific function that generates a 162-bit hash of the original message. The hashed message is secure and unique. The sender then uses the public key digital signature algorithm and his private key to sign the hash to generate a digital signature for the specific document. On receiving the digital signature and the corresponding text message, the receiver will need to calculate two separate values. First the hashed message of the received text is calculated using the same hashing algorithm. Then, once the receiver has the hash value, he can now use the decryption algorithm with the sender’s public key and digital signature to retrieve the signed hash. If the receiver is able to decrypt the digital signature, this implies that the sender’s private key was used to encrypt the hashed message. The final step for the receiver is to compare the hash calculated with the hash retrieved from the decryption process. If these two hashed messages match, then the receiver has indeed received the original message signed by the sender (thus preserving message integrity).
UNCITRAL has developed Model Laws on E-Commerce and E-Signature to provide national legislators with a set of internationally acceptable rules aimed at removing legal obstacles and increasing legal predictability for electronic commerce, and at facilitating the use of electronic signature.
Benefits
The adoption of e-signature solutions drives significant benefits:
- Provides a global electronic invoicing solution with local legal compliance.
- Supports accounts receivable and accounts payable processes.
- Eliminates a company’s capital costs to create a compliant e-invoice archive.
- Maximizes security utilizing protected invoices and highly secure connections.
- Lowers IT costs and simplifies IT infrastructure.
- Eliminates transactional barriers and invoicing issues.
But the complexity and high cost of e-signature implementations must take into account the following factors:
- There is no mutual recognition by Certification Authorities.
- Transparency is lacking concerning the grounds for acceptability of an e-signature for a cross-border trade exchange. The result is that in some countries corporations implement so-called double signatures ? one for the sender’s and one for the buyer’s own country.
- Some European countries (e.g. Germany, Italy, Poland, Portugal, Spain, and Hungary) require qualified signatures based on certificates issued to actual persons.
References
Useful reading includes the European e-Invoicing Final Report ; the European market description and analysis for e-Invoicing of the Euro Banking Association (EBA)-Innopay (2008); and the case study of a digital signature solution implementation for a healthcare organization that provides disability evaluation services for various government agencies and private companies.
